OPC UA Security
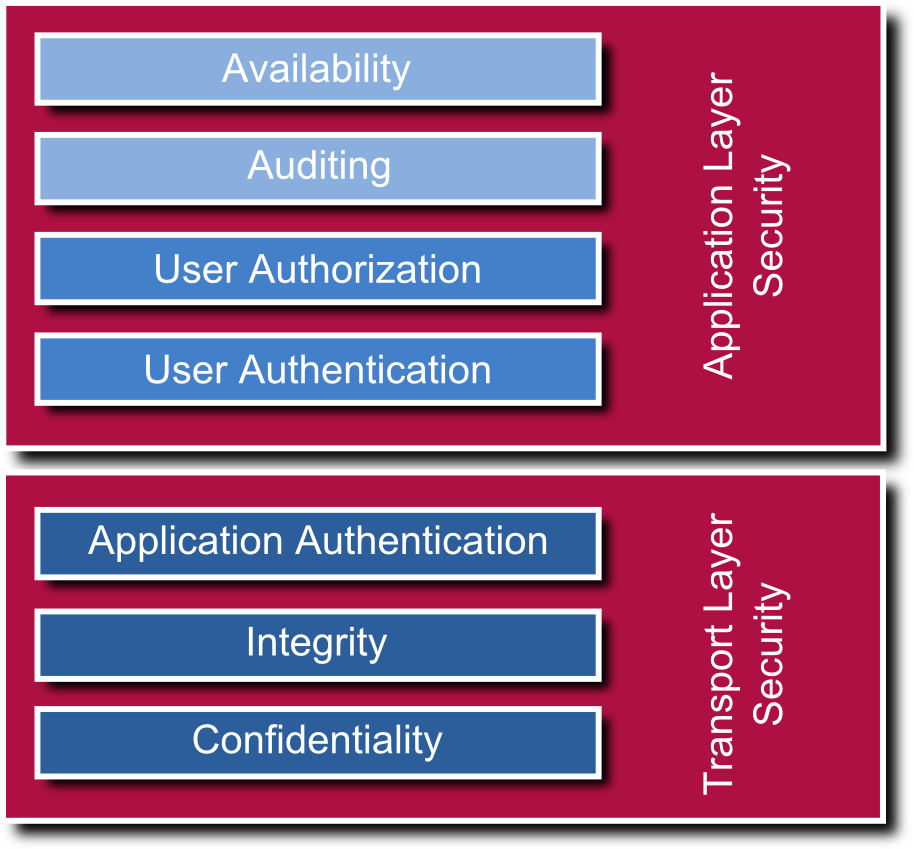
UA security is a multilayer concept. It contains authentication and authorization as well as encryption and data integrity by signing. A distinction is made between application layer and transport layer security.
There are several security mechanisms on application layer. The user or operator of an application can be identified by a user/password combination or a user certificate. The data access rights can be adjusted for each single node: It is possible that a user is only allowed to read values, whereas an administrator may also have write access, but a guest may not even be able to browse a node. In addition to that, audit mechanisms are defined and a server may log which person has changed which value at which time (audit event, audit log).
Security is not optional, the features are integral parts of the specification and the UA stack.
Transport Layer
OPC UA defines message security for the binary as well as for the web service protocol. The hybrid variant uses TLS (transport layer security) and secures the route of transport. The OPC foundation did not completely reinvent security mechanism but follows the Web Service Security Specifications. For Web Services, WS Secure Conversation is used which ensures the compatibility to .NET and other SOAP implementations. For the binary variant, algorithms of WS Secure Conversation have been adopted and converted to a binary equivalent, which is now known as UA Secure Conversation.
As shown on the figure OPC UA Protocols, there is a hybrid version using binary encoding and HTTPS for transport, being a compromise between efficient binary encoding and firewall-friendly transmission. The authentication exclusively uses x509 certificates. It’s up to the application developer to decide to which certificate store the UA application is bound to. For instance, it is possible to use the Public Key Infrastructure (PKI) of an Active Directory.